Invented by GONZALEZ; Jose Luis Merino, GONZALEZ; Jesus Ruiz, ORTIZ; Cristina Bernils

Authentication is everywhere in our digital lives. Each time we log in, make a payment, or enter a virtual space, we are asked to prove who we are. But what if current systems are not enough? Today we explore a groundbreaking patent application that offers a new way to make digital authentication more secure, more flexible, and much harder to fool. Let’s break down how this system changes the game for online security and user verification.
Background and Market Context
The way we live and work is changing fast. Smartphones, tablets, and other internet-connected devices are now part of almost everyone’s daily routine. With more people using these devices, there is also a big push to move more of life online. Companies are building virtual worlds, online banks, and digital spaces where users can interact, shop, play, and even work. With all this growth, the need to know who is really behind the screen is more important than ever.
Traditional security methods—like passwords or even simple face recognition—are starting to show their limits. Hackers keep finding new ways to break in. At the same time, we are seeing new threats. For example, what if a person falls asleep while controlling a remote vehicle? Or what if someone tries to trick a system by holding up a photo or video of someone else? The risks can be huge, from stolen money to life-or-death situations.
Big companies have invested in high-end solutions, like special cameras that use infrared light to map faces in three dimensions. But these systems are expensive, need lots of storage and processing power, and still struggle in bad lighting or with users who have certain skin tones. Most people use regular phones or tablets, which do not have these fancy features. As a result, many people are stuck with less secure options.
In this new world, security must do more than just check a face or a password. It needs to prove that the user is real, alive, and present right now. It also needs to work on everyday devices. This is where the new patent application comes in. It aims to fill the gaps left by older systems, making it easier for everyone to have strong, smart, and fair protection—no matter what device they use.
Scientific Rationale and Prior Art
Let’s look closer at how current systems work and why they aren’t good enough for today’s needs. Most biometric systems today do one of two things: they use a regular camera to grab a photo or they use a special infrared camera to map the face in 3D. The first method is simple but easy to fool. The second is better but expensive and not always reliable.
Some companies have tried to make these systems smarter. For example, they might ask a user to blink, turn their head, or read a phrase aloud. Sometimes these tests help, but often they are annoying, easy to trick, or just do not work well for everyone. Plus, these methods need good lighting and a high-quality camera.
Other systems try to check if a person is “alive” by watching for small movements or changes in the image, but these can be thrown off by glasses, lighting, or even just a low-quality phone. In some cases, these checks are so strict they lock out real users by mistake. In other cases, they are so weak they let in fakes.
One key problem is that most systems still only look at two dimensions (height and width of a face in a photo). They do not really measure depth. That makes it hard to tell the difference between a real face and a picture or video of a face. Some high-end phones use dots of infrared light to map the curves of a face, but this only works at close range, and only if the device has the right hardware.
Another challenge is fairness. Many systems work well for some skin tones but not others. This can cause big differences in how well the system works for people of different backgrounds. It can also make security weaker overall.
Finally, as more companies move into virtual spaces or rely on remote controls, the risks of someone “faking” their presence grow bigger. Imagine someone using a bot to pass as a real person, or a tired driver nodding off while steering a truck from afar. The old systems just aren’t built to handle these kinds of threats.
The patent application we are discussing points out all of these problems. It explains how current technology is too expensive, too slow, and too limited to keep up. It also shows that most systems need lots of processing power, storage, and good lighting—which are not always available. Most important, it highlights that no current system can offer strong, easy-to-use, and fair security for all users on regular devices.
Invention Description and Key Innovations
Now let’s dive into the heart of this patent application. What does it offer that is new? How does it work? And why does it matter for the future of authentication and security?
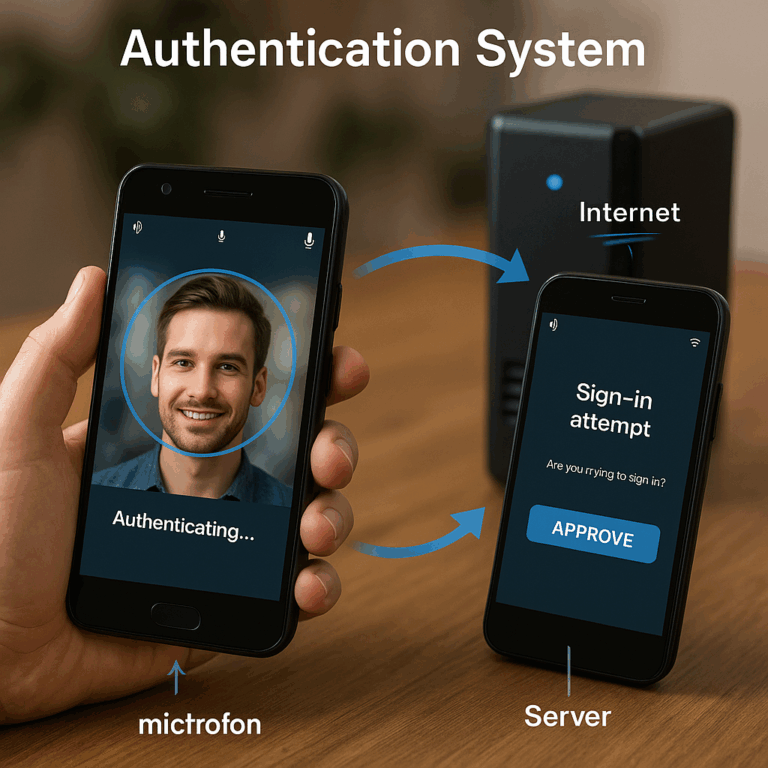
At its core, this invention combines the power of everyday devices (like phones and tablets) with smart software and cloud processing to create a new, more secure authentication system. Here’s how it breaks new ground:
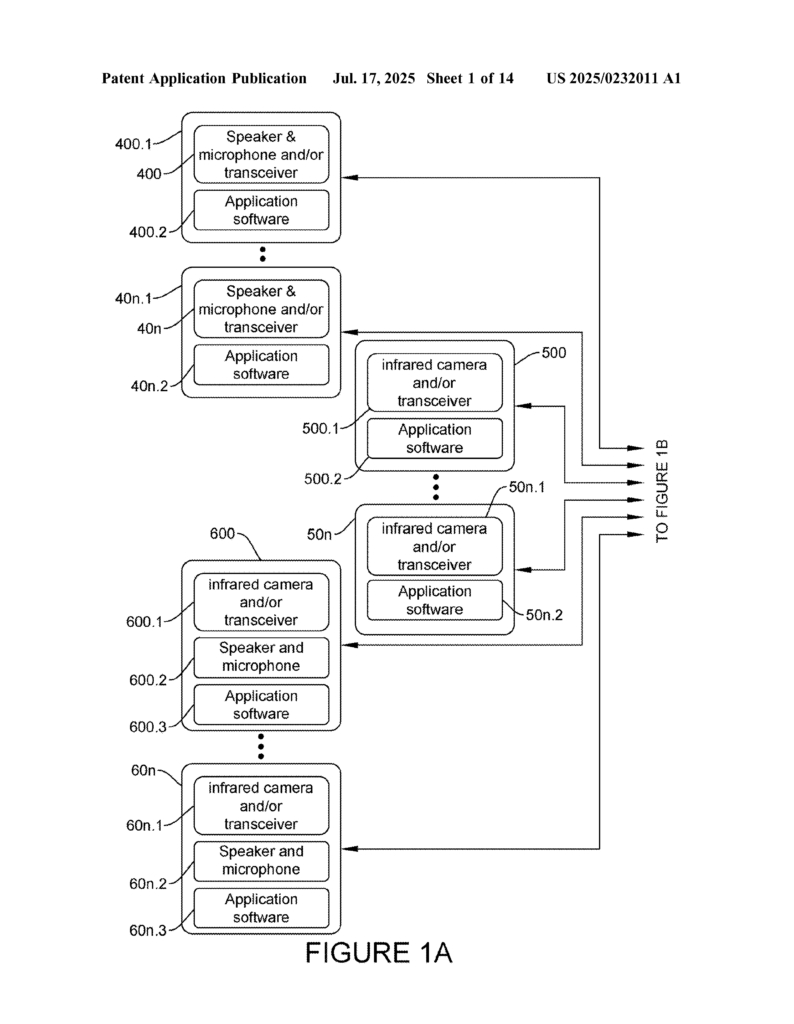
1. Multi-Modal Sensing: More Than Just a Camera
Instead of relying only on a camera, this system uses a mix of tools already built into most devices. It can use the speaker and microphone to send and listen for sound waves that “bounce” off a face or object—like a mini sonar. It can also use a camera to take multiple pictures or videos. If the device has extra sensors, like special frequency transmitters, it can use those too.
This means the system can “see” not just the surface of a face, but also its shape in three dimensions. It can even add color information as a fourth “dimension,” making the digital model of the face much richer and harder to fool.
2. Cloud Power for Smart Processing
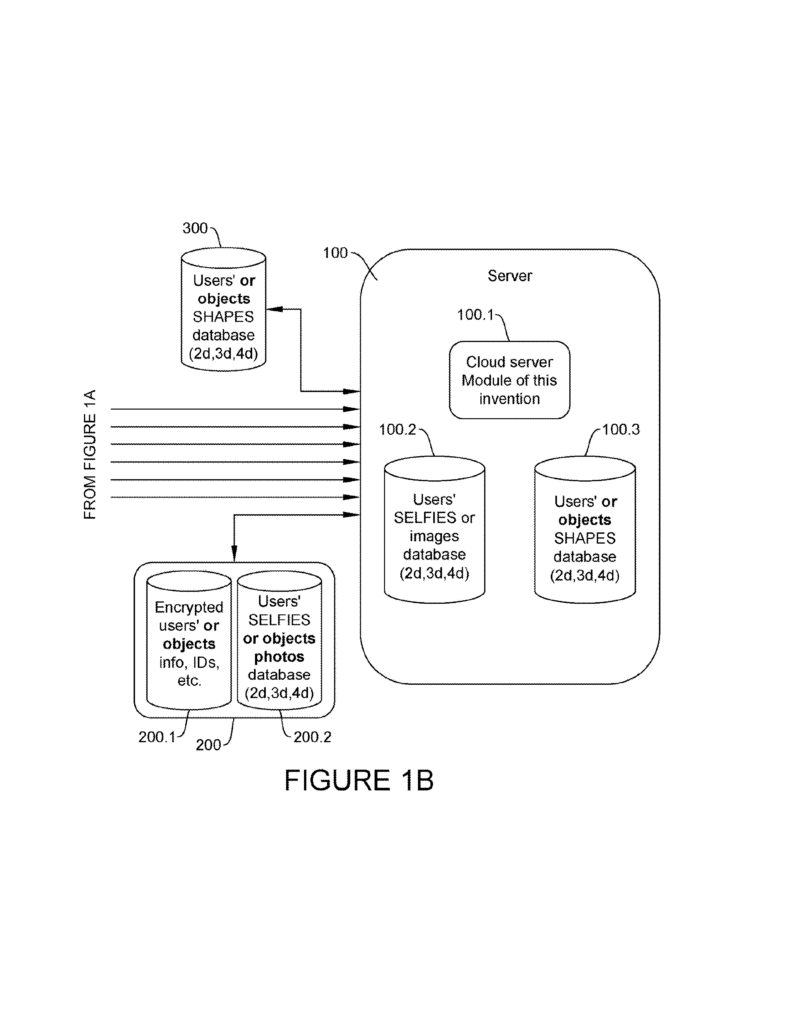
All of the data—sound waves, images, color info—gets sent to a secure server in the cloud. This server is much more powerful than any one phone or tablet. It can use artificial intelligence to process the data, build 3D (or even 4D) models, and compare them to stored records.
This approach means the heavy lifting is done off the device. Even older or lower-end phones can use the system, because they just need to collect the data and send it to the cloud.
3. Advanced Liveness Detection
One of the smartest parts of this invention is how it checks if a user is really there, awake, and alive. It does this in several clever ways:
– It measures how the eyes respond to changes. For example, it can make the screen go from dark to very bright and watch how the pupil shrinks or grows. It can also show a small object on the screen, then make it bigger, and see how the eyes adjust focus. Both the size of the pupil and the color of the eye parts are checked.
– It watches for natural actions, like blinking, and checks that the changes in the eye area match what should happen for a real person—not a photo, video, or mask.
– It groups and compares data by color, shape, and even tiny details, making it much harder to trick with printed images, videos, or fake faces.
– The system can also detect fraud by checking if the changes in the eye or face match what is normal for that user over time. If something is off (like the blink looks “wrong” or the color does not match), it can block access.
4. Flexible and Inclusive
Because the system uses a mix of signals and checks, it can work well for people with different skin tones, in different lighting, and with different types of devices. The cloud processing can adjust for small differences, making the system fairer and more reliable.
5. Action-Based Security: Not Just for Logins
The invention is not just for logging in. It can also check identity for high-risk actions, like making a big payment or changing account details. If someone tries to make a new account, the system checks if their face or eye data matches any blacklisted users or fake attempts. If so, the account is blocked. If not, the user is allowed in.
6. Smart Indexing and Data Matching
Every piece of data is stored in a way that links it to the right user and groups it by features—like color, shape, or action (such as before and after a blink). This makes searching, matching, and fraud detection faster and more accurate.
7. Real-World Use Cases
This system is built for real problems:
– Keeping online accounts safe from hackers
– Making sure only the right person can control a remote machine or vehicle
– Blocking bots or fake users in online spaces or games
– Helping companies meet legal rules for identity checks
– Making virtual worlds safer and more fair for everyone
How It All Comes Together
Imagine you want to log into your bank app. Instead of just snapping a selfie, your phone uses the speaker to emit a sound wave. The microphone listens for the echo as it bounces off your face. At the same time, the camera takes a few quick pictures, before and after you blink, or as the screen changes brightness. All this data goes to the cloud, where smart software checks if you are really you—alive, present, and not faking it.
If everything matches your stored records, you get in. If something is off, access is blocked. If a new account is being made, the system checks for matches against a database of fake or blacklisted faces. If there’s a match, no account is created.
Even if you have an older phone, the system can still work, because it does not rely on fancy hardware. All it needs is a camera, microphone, and speaker—which almost every device has.
What Makes This Invention Unique?
The real breakthrough is in the combination of methods. By using sound and image, by checking both the surface and the depth of the face, by adding color as a key feature, and by testing for real-time changes like blinking or eye response, this system is much harder to trick. It also makes smart use of cloud power, so even regular devices can offer very strong security.
It also adapts to users with different skin tones, lighting, and device types, making it more fair and accurate than many older systems. Plus, the flexible design lets companies use it for many different actions—not just logins, but also payments, account changes, and even remote control of machines.
Conclusion
Today’s world needs better, smarter, and fairer ways to prove who we are online. This patent application shows how the tools we already have—our phones, tablets, and cloud servers—can be used in new ways to keep our digital lives safe. By mixing sound and sight, using real-time tests, and harnessing powerful cloud software, this system offers a big leap forward in security and user trust.
As more of our lives move online, and as digital risks grow, inventions like this will become more and more important. They protect not just our accounts, but our money, our privacy, and even our safety. If you are a company building digital spaces, a user wanting better protection, or just someone interested in the future of security, this is a technology to watch.
Click here https://ppubs.uspto.gov/pubwebapp/ and search 20250232011.
